You've got me more curious about the device itself and a rough geographical area it was bought in. Care to share?
It does when you're sharing nationally classified information with what is a third party, not sanctioned by the administration itself?
The headquarters are irrelevant.
Is it?
Is that why people trying to protect their privacy use VPN's/DNS resolvers outside of the US jurisdiction such as Mullvad/Quad9 etc?
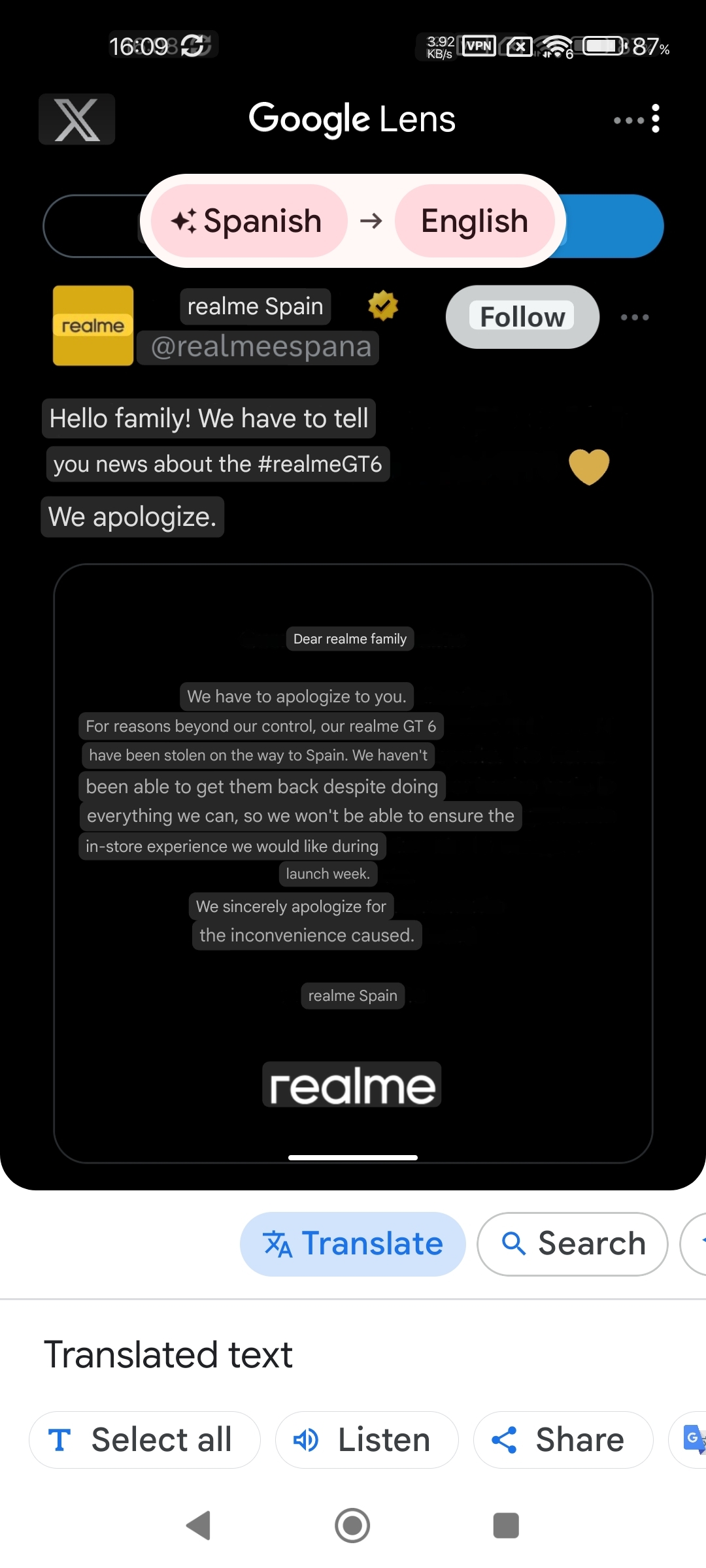
And as stated by someone else if you're using a personal device with a phone number to share classified information outside of a SCIF, you've got to ask yourself if there's a modicum of "sensibility" in the administration here.
It's like someone else said - I went back and dug a little on old.reddit (RIP r/America) and there's for some reason its "not being shared" and actually, neutered?
Maybe I'm just a sucker for popcorn but it smells like it shit, it usually is 💩
It is absolutely insane, considering they have SCIF devices / rooms but also the option of "not using off the shelf" shit like Signal and using a phone number. But here they are.
Hell, they could even use something like Briar / Matrix / whatever that is decentralised/does not require a phone number unlike Signal but instead they sent emotes, and classified information detrimental to US citizens over a centralised (third party) platform. Literally, insane.
Are we missing an /s here? Signal is headquartered in the US, and here's me pondering if they were actually using Telegram instead. Which would've been pretty apt.
I think at this point I'd be better off trying to use WeChat.....
edit: https://cloud.google.com/blog/topics/threat-intelligence/russia-targeting-signal-messenger - archive
For a bit of clarity some are not seeing. Google, sanctioned too. Crazy times.
To be fair, it's running at the top of BBC news here in the UK this morning which is kinda weird. They usually dunk stuff like this unless they too have some angle on it.
Why being MDM'ed would make it stolen?
Because companies that have already implemented MDM on a device (which your friend has) will be the first to remove any trace of them on it (data protection/GDPR etc) and if it's being sold still with the credentials of said company (with bonus malware?) you might want to poke around it a little.
As the page above states - someone is in charge of that device still and can manipulate it as per the policies they introduced when locking the phone down to an entity.
tldr: most thieves ask for FRP exploits etc to get around a MDM secured device.
If it's MDM'ed, that 99.99% of the time means it's a stolen device.
Where did they buy it from exactly?
You're gonna be on an aeroplane for a month?
e: tongue in cheek and all aren't SD cards are a thing these days? You've got the obvious network solutions but if you're off the grid?
Why bother?
Pray tell, how do you "pirate" a SSO service as you alluded to above?
No one asked for alternatives. We're more interested in how you're gonna "pirate" these things. Cheers!

Some of us love seeing dodgy devices and their nooks and crannies. If you wanna share them here, or even over on our TG * where there're many nerds from that region still ;)
t.me/randroidtg